- Starter
- Solo
- Admin
- Pro
| Starter | Solo | Admin | Pro | |
Free For Life | $1995 Per Year | $4995 Per Year | $9995 Per Year | |
| Websites included | 1 | 1 | Up to 5 | Up to 30 |
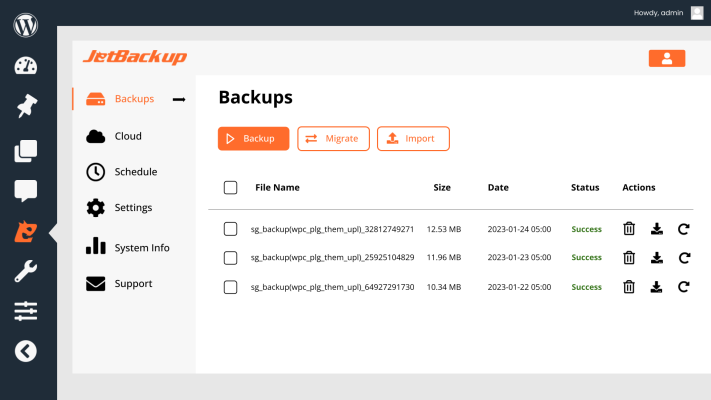
| Website backup & restore | ||||
| Website migration | ||||
| Scheduled Backups | ||||
| Backup download & import | ||||
| Remote Destinations (SFTP/FTP, Google Drive, Amazon S3, Dropbox, OneDrive, Box, pCloud) | ||||
| Custom S3 Cloud Destination | ||||
| Set Backup Retention Limit | ||||
| Email Notifications | ||||
| 24 / 7 Premium Support | Try Now | Buy Now | Buy Now | Buy Now |